Managing Secrets
What do I mean by secrets
- Passwords
- API keys
- TLS certificates
- Tokens
Why is this an important issue?
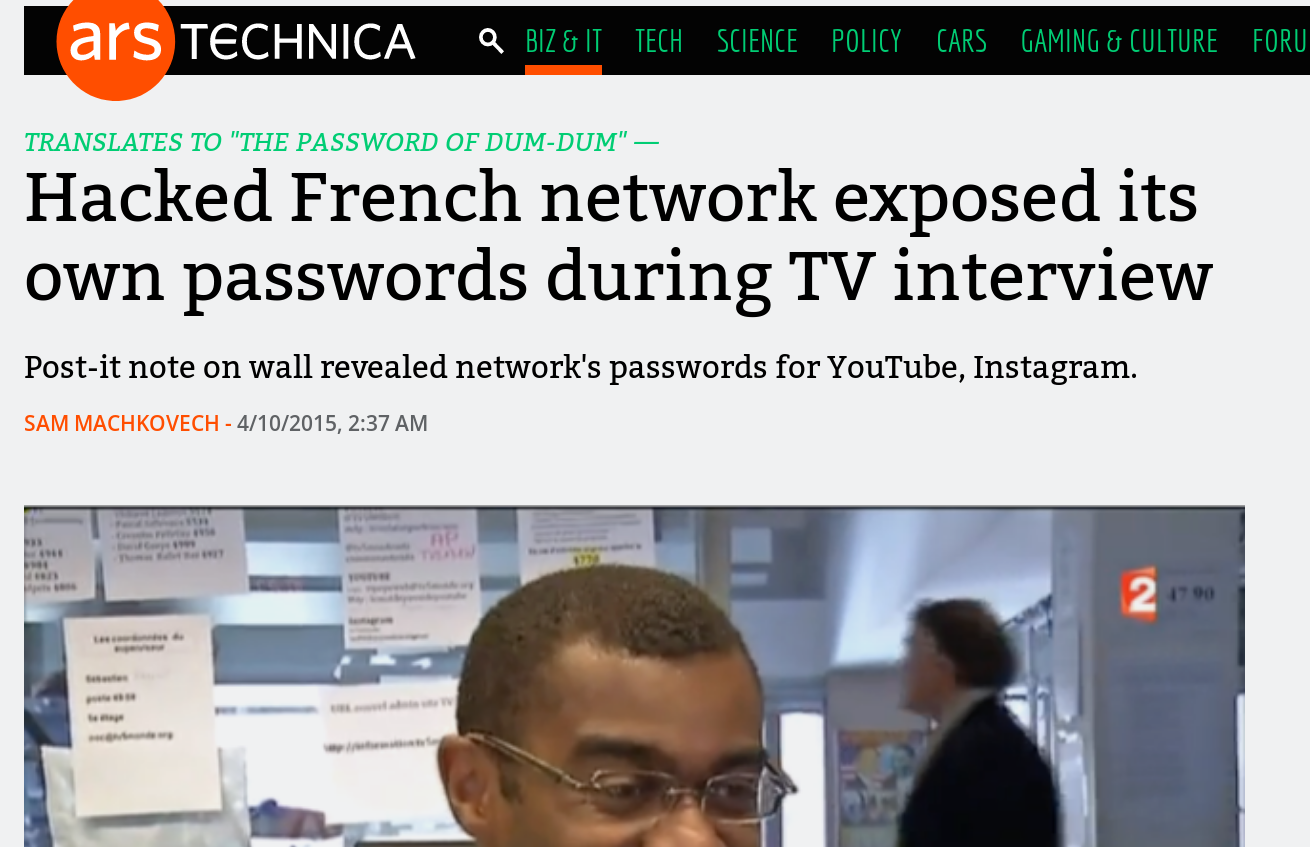
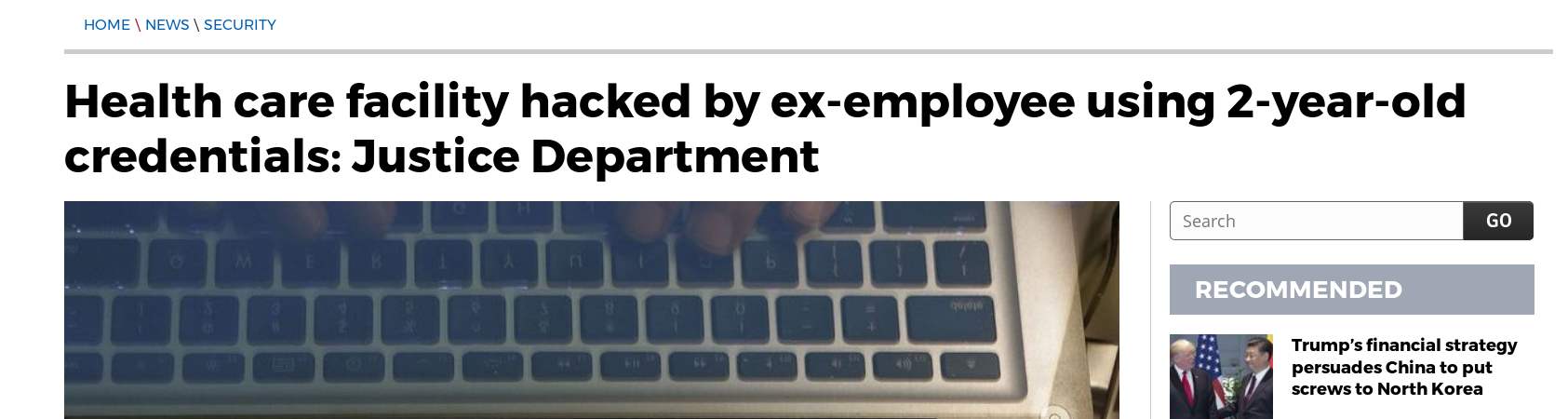
Lets focus on the things that are under the
responsibility of Dev and Ops teams
Common approaches
Place all the secrets in environment variables
- Copy configuration files to all assets
- Place all the secrets in the same file and encrypt it
- Keep adding keys to the authorized_keys files on several machines
How should it be done?
Depends on the threat model
- Secrets should never be in plain text, nor on transit or at rest.
- Principle of the least privilege
- Granular access control (defined by policy)
- Easily allow to rotate the secrets
- Every action must leave a trail
- Have a "break glass" procedure
Recently there was a surge in this area
Lets take Vault
- Stores your secrets encrypted
- Key-rolling
- Audit Logs
- Leasing
- Revocation
- Multiple backends for dynamic secrets
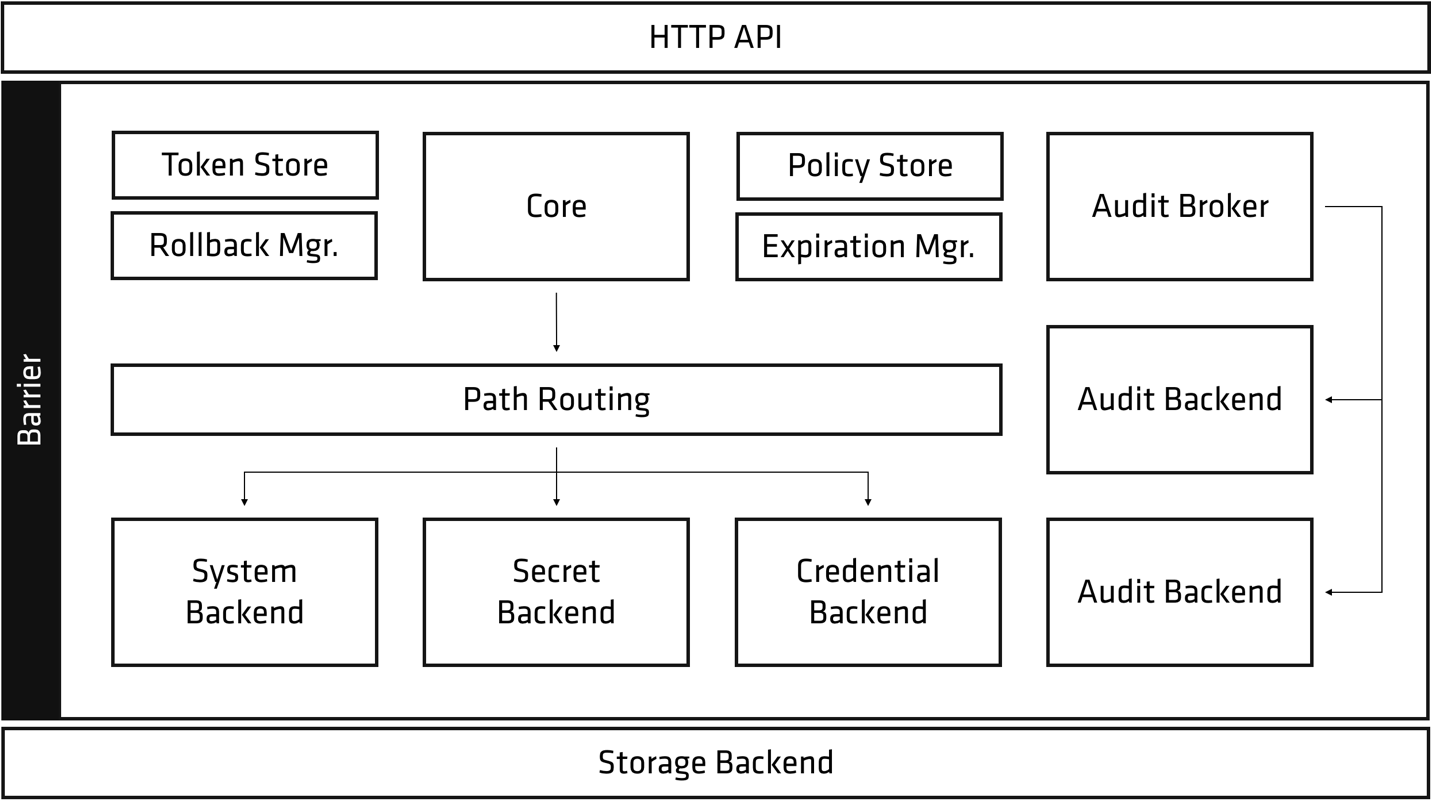
Demo time
Sources and other extra information
You can reach me through:
Website: ovalerio.net
Email: gon@ovalerio.net
Mastodon: @dethos@s.ovalerio.net
Freenode: dethos