HTTP Security Headers
A Review
Drafted by: Gonçalo Valério. Fediverse / Github
Overview
- HTTP Headers?
- Current Security Headers
- Upcoming Security Headers
- Discussion
$ telnet meetup.com 80
GET /Madeira-Tech/events/267474832/ HTTP/1.1
Host: www.meetup.com
Cache-Control: no-cache
$ openssl s_client -connect meetup.com:443
GET /Madeira-Tech/events/267474832/ HTTP/1.1
Host: www.meetup.com
Cache-Control: no-cache
HTTP/1.1 200 OK
Content-Type: text/html; charset=utf-8
x-frame-options: SAMEORIGIN
accept-ranges: bytes
Set-Cookie: BID="id=bd09c108..."; path=/; domain=.meetup.com
Content-Length: 314616
...
{response_html}
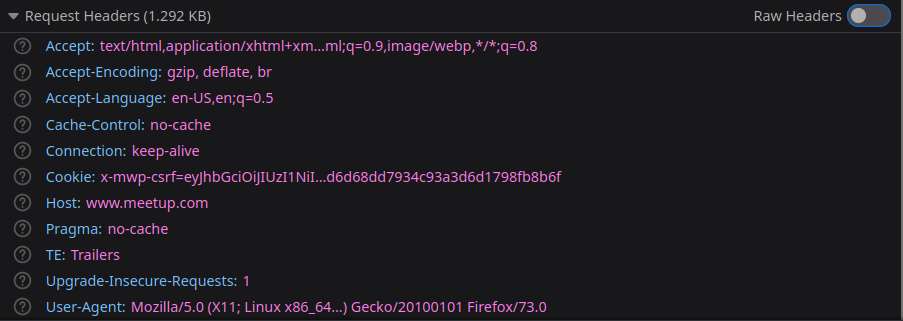
X-Frame-Options
Prevent clickjaking- X-Frame-Options: DENY
- X-Frame-Options: SAMEORIGIN
- X-Frame-Options: ALLOW-FROM(Obsolete)
“The frame-ancestors directive obsoletes the X-Frame-Options header. If a resource has both policies, the frame-ancestors policy SHOULD be enforced and the X-Frame-Options policy SHOULD be ignored.”
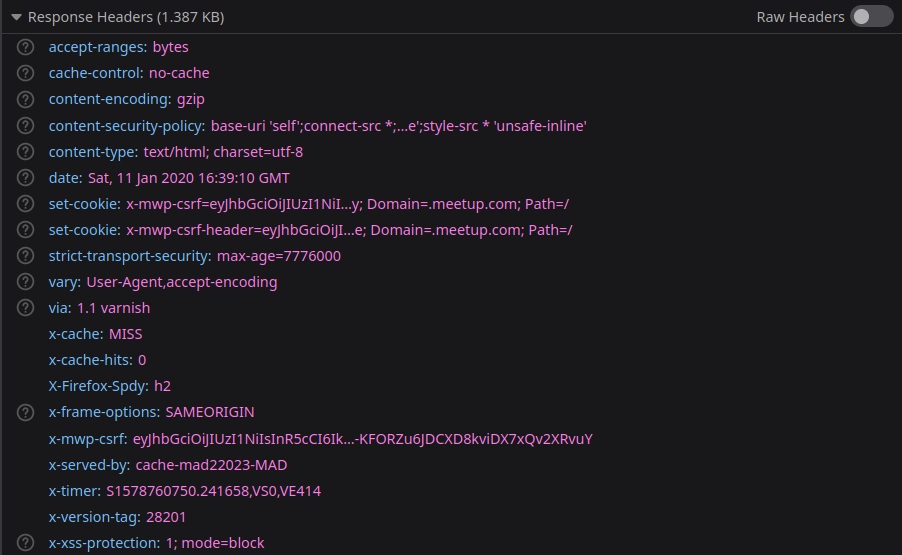
X-XSS-Protection
Detect reflected XSS- X-XSS-Protection: 0
- X-XSS-Protection: 1
- X-XSS-Protection: 1; mode=block
- X-XSS-Protection: 1; report=<uri> (Chrome only)
Only supported by: Internet Explorer, Chrome and Safari.But is on its way out.
X-Content-Type-Options
Avoid MIME sniffing- X-Content-Type-Options: nosniff
Strict-Transport-Security
Protect against SSL Strip and other MITM attacks
- Strict-Transport-Security: max-age=<seconds>
- Strict-Transport-Security: max-age=<seconds>; includeSubDomains
- Strict-Transport-Security: max-age=<seconds>; preload
https://hstspreload.org/
Content-Security-Policy
Protect against all kinds of XSS- Content-Security-Policy: {policy}
- <meta http-equiv="Content-Security-Policy" content="{policy}">
- Content-Security-Policy-Report-Only: {policy}
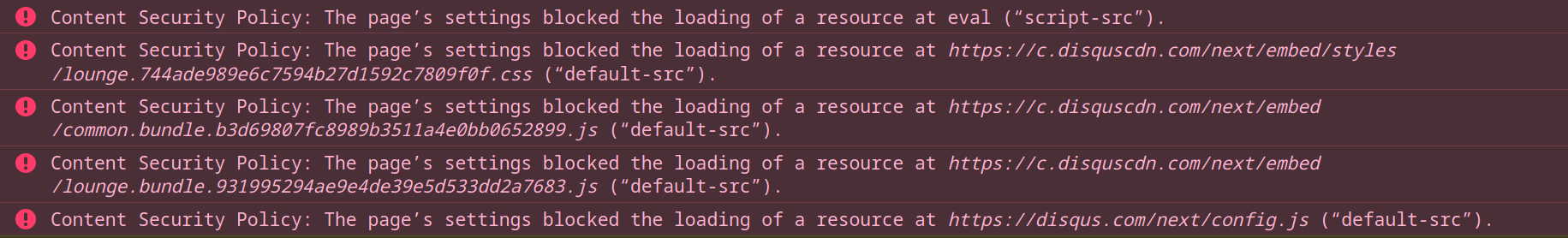
Content-Security-Policy: base-uri 'self';connect-src *;
default-src 'self' *.meetup.com *.dev.meetup.com:8001;
font-src * data:;frame-ancestors 'self';frame-src *;
img-src * data: blob:;
script-src * 'unsafe-eval' 'unsafe-inline';
style-src * 'unsafe-inline'
Content-Security-Policy: default-src 'self';
style-src 'self' 'unsafe-inline';
img-src 'self' data:; connect-src 'self';
object-src 'none'; base-uri 'none';
{
"csp-report": {
"document-uri": "http://example.com/signup.html",
"referrer": "",
"blocked-uri": "http://example.com/css/style.css",
"violated-directive": "style-src cdn.example.com",
"original-policy": "default-src 'none'; style-src cdn.example.com; report-uri /_/csp-reports"
}
}
Referrer-Policy
Privacy- Referrer-Policy: no-referrer
- Referrer-Policy: same-origin
- Referrer-Policy: unsafe-url
There are other intermediary options.
SameSite Cookies
Protect against CSRF- Set-Cookie: key=value; SameSite=Strict
- Set-Cookie: key=value; SameSite=Lax
- Set-Cookie: key=value; SameSite=None
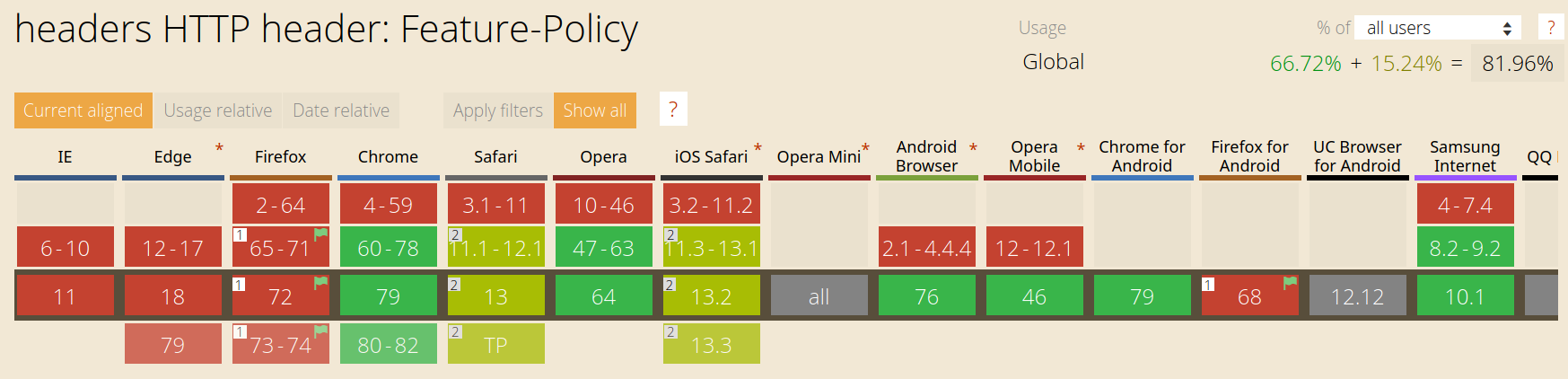
Feature-Policy
- Feature-Policy: microphone 'none'; geolocation 'self'; fullscreen https://meetup.com
Public Key Pinning
Precaution against compromised CAs- Public-Key-Pins: pin-sha256="{hash}"; max-age={seconds}; includeSubDomains; report-uri="{url}"
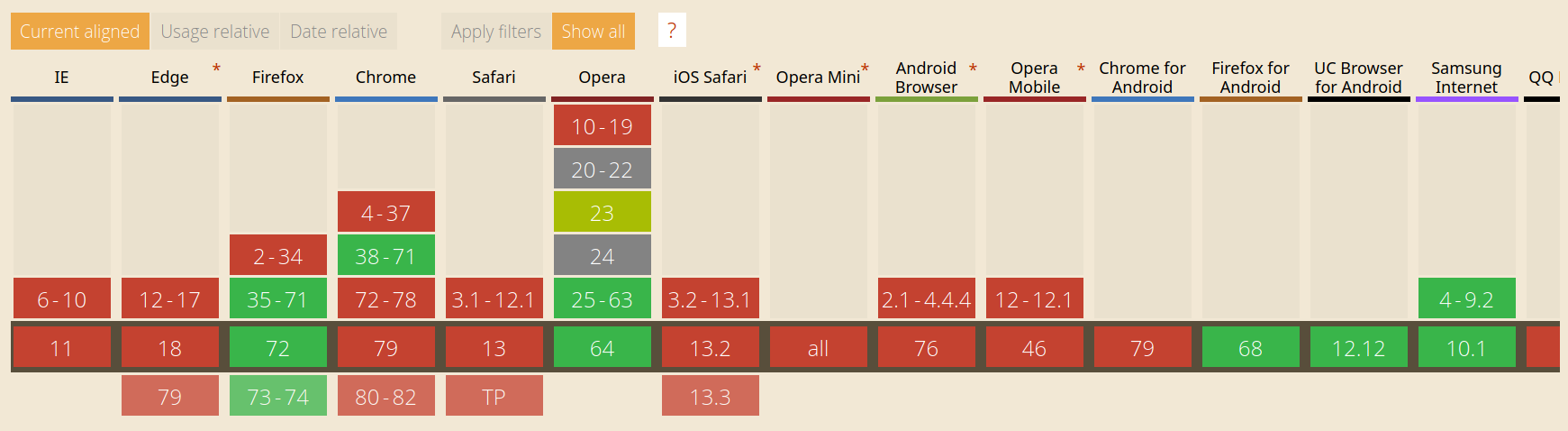
Expect-CT
- Expect-CT: max-age={seconds}, enforce, report-uri="{url}"
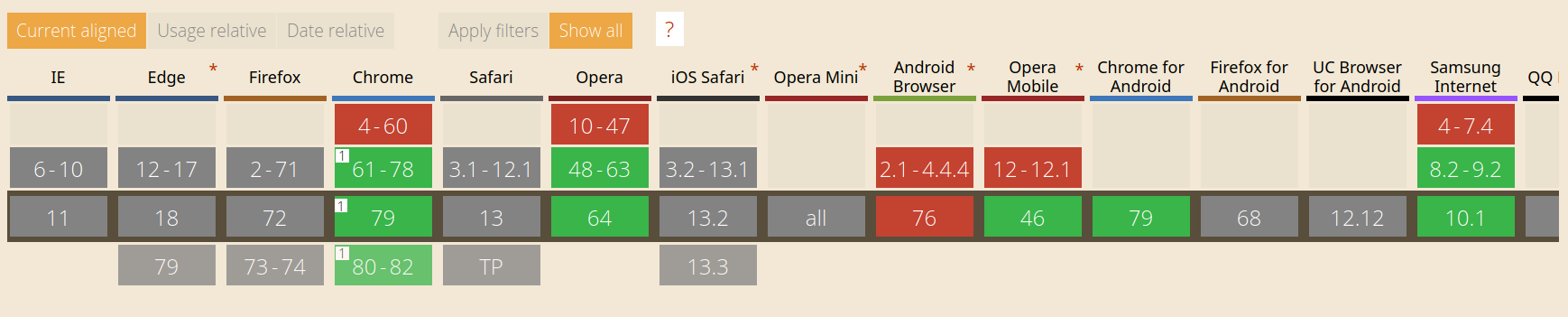
Questions
Useful links