Getting started with GPG
A 20 minute tour
Drafted by Gonçalo Valério / @dethos
Disclaimer:
- This presentation only covers the basics
- I will try to answer all questions
... but without any guarantees
What will be covered:
- A little bit of the background
- How it works
- Why and when you should use it
- How to find other people's keys
- Should you trust a given key?
Generate keys for everyone
Background
- "Pretty Good Privacy" was created in 1991 by Phil Zimmermann
- He was sued at the time. Munitions export, they said.
- Standard proposed to IETF around 1997
- The free software foundation made a compliant program (GNU Privacy Guard)
How it works? (light version)
- Bob generates a key-pair (public and private keys)
- Bob publishes his public key
- Alice can use bob's public key to encrypt messages to Bob
- Alice uses her private key to sign the message so Bob can verify it was sent by her
In what situations it is useful?
- Share sensitive material over a insecure network
- Encrypt Files
- Verify the source of a given message
Managing Keys and trust
- GPG lets you manage the keys from several people
- You can also sign them to avoid tampering
- If key was signed by someone you already signed their key, probably you can trust them
A small note about the web of trust
We will not address this concept today, but I would like to make clear that in this model does have a central authority that can verify to you that a key is valid and belongs to someone. So people need check for themselves or trust who's already been signed by someone you know.
Lets give it a try
Download the required software
| Platform | Cli | Gui |
|---|---|---|
| Linux |
gpg/gpg2
|
Kgpg
|
| Mac OSX |
gpg2
|
GPG Suite |
| Windows | Lets forget about the CLI | Gpg4win |
Generating the keys
$ gpg --gen-key
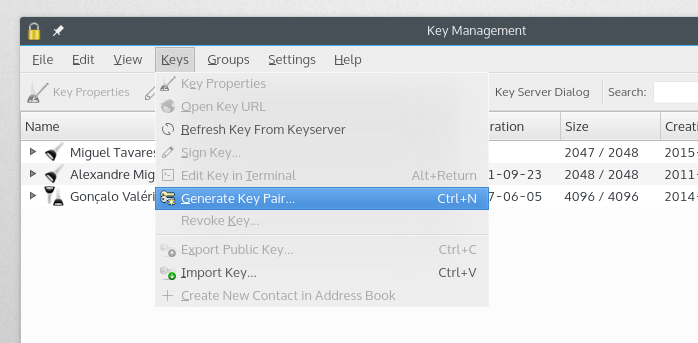
$ gpg --list-keys
Lets add the following parameters:
- 4096 bit keys
- Set an expiration date (2 years for example).
- Do not forget to provide a strong pass-phrase
-
In the end generate a revocation certificate:
$ gpg --output revoke.asc --gen-revoke your_key_id
Share the keys
To send your key to the key server so others can retrieve it and sign it you must execute the following command:
$ gpg --keyserver pgp.mit.edu --send-key your_key_id
Import and Export public keys
gpg --output key_file.gpg --export your_key_id
gpg --import key_file.gpg
Encrypt and Decrypt
gpg --output doc.gpg --encrypt --recipient dest_key doc
gpg --output doc --decrypt doc.gpg
Revocation
For any reason if you lose you private key or forget the paraphrase. Use your revocation file:
gpg --import revoke.asc
gpg --send-key --keyserver pgp.mit.edu key_id
Integrate with your email client
There are several plugins and apps that support GPG and can automate all this work.
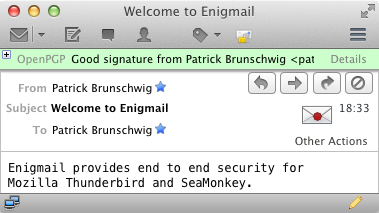
- Enigmail
- GPG Suite for Apple mail
- For webmail clients there are browser extensions such as Mailvelope